When a single individual or a small group gains control over the majority of a blockchain network’s power, it compromises the foundation of blockchain security and decentralization, creating the perfect conditions for a 51% attack. In such an attack, the attacker can reverse transactions, double spend coins, and even rewrite the blockchain’s history, undermining its entire security framework.
This not only erodes user trust in the blockchain but also risks users withdrawing from the market to protect their assets or switching to rival blockchain networks. In this article, we’ll explain how a 51% attack occurs, which networks are most vulnerable, and the impact on Proof of Work security and user confidence. If you want to learn how an attacker can bypass the seemingly impenetrable blockchain system, keep reading.
Key Points:
|
What is a 51% Attack and How Does It Work?
A 51% attack is one of the most significant security threats to blockchain networks. This attack occurs when an individual or group gains control of more than 51% of the network’s computational power (hash rate). With this level of control, they can manipulate various aspects of the network’s operations.
For example, they can:
- Prevent new transactions from being confirmed.
- Reverse certain transactions and double spend the same cryptocurrency.
- Alter the order of blocks and present a fake version of the blockchain (reorganization of blocks).
In networks using the Proof of Work (PoW) consensus algorithm, an attacker controlling more than 50% of the computational power can execute a 51% attack. Similarly, in Proof of Stake (PoS) networks, an attacker with control over more than 50% of the staked coins used for validation can also carry out a 51% attack.

Steps of a 51% Attack Explained Simply
Let’s go through the steps involved in a 51% attack, a significant blockchain security threat, in a simple, step-by-step manner.
Gaining Over 50% of the Network’s Computational Power (Hash Rate Control)
The first step in a 51% attack is for the attacker to gain control of more than 50% of the network’s computational power (hash rate). This can be done in several ways:
- Purchasing a large number of mining devices, such as ASICs (for Bitcoin) or GPUs (for other cryptocurrencies).
- Attracting miners to join a mining pool controlled by the attacker.
- Renting hash rate control from websites that provide mining services.
The smaller and weaker the network, the easier and cheaper this step becomes. A 51% attack is harder to execute on larger, more established blockchains like Bitcoin, where the Bitcoin 51% attack cost would be incredibly high.

Isolating from the Network (Private Blockchain)
Once the attacker gains control, they begin mining blocks independently and start building a private blockchain. This private chain is kept separate from the public network, creating a hidden version of the blockchain.
Building a Parallel Blockchain to Perform Double Spending
The attacker starts mining a parallel blockchain, beginning from a block just before the targeted transaction. This allows them to later overwrite the public chain and perform double spending, where the same cryptocurrency is spent more than once. Essentially, two blockchain versions emerge: one visible to all users and one controlled by the attacker.

Making a Transaction and Receiving Goods or Money
The attacker carries out a transaction on the public blockchain (e.g., sending cryptocurrency to purchase goods). Once the goods or services are received, they reveal their private blockchain, one that does not include the transaction. This results in a double spending attempt, as the transaction is effectively erased from the private chain.
Forcing the Fake Blockchain onto the Network (Reorganization of Blocks)
Since the attacker’s private blockchain is longer (due to more computational work), the network, following consensus rules, accepts it as the valid chain and discards the previous one. This process is known as a block reorganization, or Reorg.
In Proof of Work Security networks like Bitcoin, the cost to perform a 51% attack is very high due to the large hash rate required to control more than half of the network. However, in Proof of Stake (PoS) networks, the attack method differs. Instead of controlling computational power, the attacker needs to control over 50% of the staked tokens used for validation.
What is the Cost of a 51% Attack?
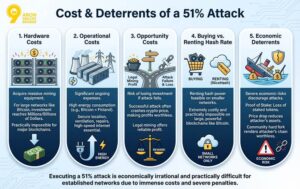
Executing a 51% attack on a blockchain network is extremely expensive, but the exact cost depends on the size and strength of the network. The larger and more powerful the network, the harder and more costly it is to launch such an attack. Below, we explain the different costs an attacker must consider:

Hardware Costs
To carry out a 51% attack, especially on networks using Proof of Work security, the attacker must acquire a large amount of mining equipment. The costs of this equipment vary depending on the type of network.
For large networks like Bitcoin, just the cost of purchasing mining hardware can reach millions or even billions of dollars. This level of investment makes a 51% attack on large blockchains like Bitcoin practically impossible or extremely difficult to execute.
Operational Costs
Purchasing mining equipment is just the beginning for an attacker. To set up operations, they must also account for significant ongoing expenses. The energy consumption of mining equipment is very high; for example, Bitcoin mining consumes as much energy as a country like Finland.
Additionally, the equipment must be installed in a large, secure location with proper ventilation and a stable electricity supply. The devices may need repairs or replacements, and a reliable, high-speed internet connection is essential for continuous mining activities.

| In networks like Ethereum 2.0, which use economic finality, large token holders (whales) could potentially carry out a 51% attack without needing to control 51% of the validators. This could happen even with a limited penalty. |
Opportunity Costs
An attacker could instead use the same mining equipment to mine legally and earn a reliable profit. However, if the attack fails, there is a significant risk of losing all the investment. Even if the 51% attack is successful, it often leads to a drastic drop in the cryptocurrency’s price, which can make any potential profits worthless. Therefore, in many cases, even a successful attack results in a loss for the attacker.
Buying vs. Renting Hash Rate
Some attackers may reduce costs by renting hash power from services like NiceHash instead of purchasing expensive mining equipment. This approach is relatively inexpensive and feasible on smaller networks with lower hash rates. However, on larger and more powerful blockchains like Bitcoin, even renting hash rate is extremely costly and practically impossible to execute.

Economic Deterrents
Economic deterrents also play a crucial role in reducing attackers’ motivation. Even if an individual has the financial resources to execute a 51% attack, the serious economic risks involved may discourage them.
In Proof of Stake networks, an attacker could lose all of their staked tokens if detected. Additionally, the attack could lead to a severe drop in the price of the targeted cryptocurrency, reducing the attacker’s assets.
| On top of this, the community of users may decide to hard fork the blockchain to counter the attack, rendering the attacker’s chain worthless. These factors make it economically irrational to carry out a 51% attack, even if it’s technically feasible. |
What is the Likelihood of a 51% Attack?
The likelihood of a 51% attack depends on the type of blockchain, the size of the network, and how power is distributed across it. In large, robust blockchains, the probability of such an attack is very low, as executing it requires massive financial and technical resources.
In contrast, smaller blockchains with lower hash rate control are more vulnerable, as 51% attacks are easier and cheaper to carry out. In these networks, if a few mining pools or groups control a significant portion of the network’s power, the likelihood of a 51% attack increases substantially.

Is a 51% Attack Possible on the Bitcoin Network?
Yes, theoretically, a 51% attack on the Bitcoin network is possible, but in practice, it is incredibly difficult, costly, and nearly impossible.
To execute such an attack, the attacker would need to acquire a massive number of miners, consume a tremendous amount of electricity, and set up an extensive technical infrastructure. It is estimated that just acquiring the necessary equipment would require billions of dollars in investment.
Moreover, Bitcoin is one of the most decentralized blockchain networks in the world, with thousands of miners operating globally. This widespread distribution of hash rate control makes it nearly impossible for any single individual or group to control the majority of the network.
Historically, the only concerning instance occurred in 2014 when a mining pool called GHash.IO briefly controlled around 55% of the network’s hash rate. This prompted the Bitcoin community to raise alarms, and many miners left the pool to restore balance to the network.

Which Cryptocurrencies Are Most Vulnerable to a 51% Attack?
Cryptocurrencies with smaller networks, lower hash rate control, or higher mining concentration are more susceptible to a 51% attack. In other words, the less decentralized a blockchain is, and the fewer or weaker the miners are, the easier and cheaper it becomes to execute such an attack.
In fact, emerging or low-traffic blockchains that still have limited hash rate are more attractive targets for attackers. In these networks, an individual or group with relatively modest investment can gain control of a large portion of mining power and manipulate transactions or even execute double spending.

| In many blockchains, an attacker can manipulate the network’s behavior by creating multiple fake nodes in the Gossip Layer, diverting the chain’s behavior by intentionally spreading misleading information. |
Why Are Altcoins More Vulnerable to a 51% Attack?
In many altcoins, mining is not as distributed and decentralized as Bitcoin. For instance, only a few large mining pools may control a significant portion of the mining power. In such cases, if one pool, or a coalition of pools, gains majority hash rate control, a 51% attack becomes entirely feasible.
Additionally, because the market value of some altcoins is lower, attackers can execute a 51% attack with lower risk and a smaller investment. In these networks, attackers can even profit from double spending, manipulating transactions to their advantage.
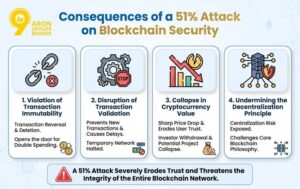
Consequences of a 51% Attack on Blockchain Security
A 51% attack can have severe consequences on the security of a blockchain network, leading to a significant loss of user trust. The impacts of such an attack include:
- Violation of Transaction Immutability: One of the key features of blockchain technology is the immutability of transactions. In a 51% attack, the attacker can reverse or delete previously confirmed transactions, creating an opportunity for double spending. This can be one of the most dangerous threats in systems relying on Proof of Work security or any other consensus mechanism.
- Disruption of Transaction Validation: When an attacker gains control over more than 50% of the network’s hash rate control, they can prevent new transactions from being validated or selectively approve only their own transactions. This can cause significant delays or even a temporary shutdown of the network’s ability to process transactions, severely affecting its performance.
- Collapse in Cryptocurrency Value: The occurrence of a 51% attack often leads to a drastic reduction in user trust, which in turn can cause the cryptocurrency’s value to plummet. This could result in investors withdrawing their funds, a sharp decrease in user activity, and possibly even the end of the project. The collapse in value is one of the key consequences of such attacks, as seen in 51% attack examples like Ethereum Classic and Bitcoin Gold.
- Undermining the Decentralization Principle: A 51% attack also reveals the risks associated with too much centralization in mining or validation. If a single group controls a majority of the hash rate, the Proof of Work security model is compromised, which fundamentally questions the decentralization and trustless nature of the blockchain. This attack demonstrates the critical importance of decentralization in blockchain’s security and integrity.
Examples of 51% Attacks in Various Blockchains
A 51% attack is not just a theoretical threat; in recent years, several networks have actually fallen victim to it. Below are some real-world examples of 51% attacks:
Bitcoin Gold (BTG) – May 2018
One of the most well-known examples occurred with Bitcoin Gold (BTG) in May 2018. In this attack, the attacker gained control of the majority of the network’s hash rate control, rewrote the transaction history, and double spent nearly $18 million worth of BTG. This attack severely damaged user trust and caused a significant drop in the market value of the cryptocurrency.
Ethereum Classic (ETC) – August 2020
Another important example is Ethereum Classic (ETC), which has been targeted by 51% attacks multiple times. In one such attack in August 2020, the attacker controlled mining and double spent over $5.6 million worth of ETC. This attack resulted in widespread distrust and reduced the network’s security.

Vertcoin (VTC) – December 2018
Vertcoin (VTC) also suffered a 51% attack in December 2018. In this attack, about 603 Vertcoins were double spent, worth around $100,000 at the time. The attacker created a longer chain, removed previous transactions, and rewrote the blockchain to their advantage.
Bitcoin Cash (BCH) – 2018 Incident
Interestingly, even Bitcoin Cash (BCH) experienced a similar incident. In 2018, two mining pools, BTC.com and BTC.top, gained control of over 50% of the network’s hash rate to halt the activities of an anonymous miner. While this action was ostensibly taken for security reasons, it demonstrated that even collaboration between mining pools could lead to a 51% attack.

Comparing a 51% Attack to Other Blockchain Attacks
A 51% attack is one of the most well-known blockchain threats, but it is not the only type of attack. To better understand its significance, it’s important to compare it to other common attacks in blockchain networks and see why it is considered more specific or dangerous.
In a 51% attack, the attacker directly targets the consensus mechanism and the core structure of the network, the very elements that ensure blockchain security. In contrast, other attacks often exploit weaknesses in the design, implementation, or structure of the network. Some of these attacks include:
Sybil Attack
A Sybil attack occurs when an attacker creates fake identities within the network to alter voting or decision-making in their favor. This attack is more common in Proof of Stake networks and blockchain systems based on voting mechanisms. However, unlike a 51% attack, a Sybil attack does not have the capability to manipulate blocks or perform double spending.
Selfish Mining
Another type of attack is selfish mining. In this attack, miners secretly mine new blocks and release them later in order to gain more rewards. Unlike a 51% attack, the goal of selfish mining is not to rewrite transactions but to secure more mining rewards. However, it still damages the fairness of the network and undermines its overall functionality.
Smart Contract Exploits
Smart contract exploits are attacks that primarily occur in networks like Ethereum, exploiting bugs or vulnerabilities in the code of smart contracts. These attacks usually don’t harm the entire blockchain but can result in the direct theft of assets from specific projects or smart contracts.
In blockchains where data is anchored to another chain, a 51% attack can result in the registration of a fake blockchain in the reference blockchain without that fake chain actually being valid.
Why the 51% Attack is the Most Dangerous
In a broad comparison, a 51% attack is the only attack with the real potential to rewrite blockchain history, which can destroy the very foundation of trust across the entire network. While other attacks are typically either limited to specific projects or users or do not directly affect the structure of the network, a 51% attack undermines the integrity of the whole system.
For this reason, a 51% attack is considered one of the most dangerous scenarios in blockchain, as it not only causes financial damage but also questions the credibility, trust, and security of the entire network.

Preventive Measures Against a 51% Attack
There are several strategies that can help strengthen the security of blockchain networks against a 51% attack. While completely preventing this type of attack is never easy, technical and structural methods can significantly reduce its likelihood. Some of these strategies include:
Changing the Consensus Algorithm
One of the most important solutions is to change the consensus algorithm. Blockchains that use Proof of Work (PoW) are more vulnerable to 51% attacks due to the concentration of mining power in a few pools. On the other hand, using Proof of Stake (PoS) can reduce this risk. In PoS, the attacker would need to purchase and lock a significant portion of the network’s tokens, which is costly and makes executing the attack more difficult.
Delaying Blockchain Confirmations
Another approach is to increase the time taken for transaction confirmations. If blockchain confirmations are delayed slightly, it will be easier for the network to identify and neutralize an attack. Additionally, the attacker would need to maintain control over 51% of the network for a longer period, increasing both the cost of the attack and the likelihood of failure.
Penalty System
In Proof of Work networks, a penalty or slashing system can be implemented. In this system, if a miner behaves maliciously or fails to validate correctly, their staked tokens are partially or fully confiscated. This financial punishment reduces the incentive for 51% attacks and encourages miners to follow the network’s rules.
Regular Blockchain Protocol Audits
Finally, regular security audits are crucial in preventing 51% attacks. Continuous examination of the network’s code and protocol by security experts can help identify and fix vulnerabilities before they are exploited. This proactive approach closes potential avenues for a 51% attack and enhances the overall blockchain security.
Conclusion
A 51% attack is not just a theoretical threat; it is a real risk that lurks beneath the surface of many small and even large blockchains. This attack directly targets the core of blockchain security, trust, and decentralization, and if it occurs, it has the potential to destroy the value of a network in a matter of hours.
Although executing a 51% attack on large networks like Bitcoin is nearly impossible due to astronomical costs and widespread power distribution, many altcoins are still vulnerable to this threat. Understanding how this type of attack works and using the right security tools can play a vital role in protecting the assets and credibility of blockchain projects.